- Keytool Pem To Jks
- Convert Pem To Jks Windows
- Convert Pem To Jks Using Keytool
- Create Jks From Pem
- Openssl Pem To Jks
- Openssl Convert Pem To Jks
If you need to create an integration that consumes external REST APIs hosted on a two-way, SSL-enabled server, you must create the keystore file required for establishing an Oracle Integration identity to facilitate a two-way, SSL-based integration. Ensure that the server on which the external REST APIs are hosted is enabled for two-way SSL support. Use Java version 1.8 or higher.
Keytool Pem To Jks
Convert Pem To Jks Windows
Openssl x509 -inform der -in pathtoDERcertificate-out pathtoPEMcertificate Convert a.pfx file to a JKS store. To convert the PEM-format keys to Java KeyStores: Convert the certificate from PEM to PKCS12, using the following command: openssl pkcs12 -export -out eneCert.pkcs12 -in eneCert.pem. You may ignore the warning message this command issues. Enter and repeat the export password.
You can obtain the client certificate in a variety of ways. Select the method that is best for your environment. For example, you can obtain the certificate directly from many certificate authorities. The steps in this section describe how to generate a certificate signing request (CSR) and have it signed by a well known certificate authority.
Note:
Inbound (trigger-based) two-way SSL is not supported.Commonly Used Terms and Tools
| Term | Description |
|---|---|
| Secure socket layer (SSL) and Transport Layer Security (TLS) | SSL and TLS, its successor, are protocols for establishing authenticated and encrypted links between networked computers. |
| Digital certificate | A data file that holds the cryptographic key provided to an organization or entity by a trusted authority. A simple analogy is a driver's license. The license uniquely identifies the person to whom it is issued. The license is issued by the DMV, a trusted authority. |
| Certificate | A public key and private key form a pair used to encrypt and decrypt data. Public keys can be freely given to anyone who needs to securely exchange data. Private keys must never be shared and must be stored securely. If private keys are listed or compromised, the issuing certificate authority must be notified so they can be added to the certificate revocation list. |
| Certificate authority (or certification authority) | An entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. |
| Certificate encoding/formats |
|
| TrustStore | A password-protected repository for trust or public certificates. The default location in Java is $JAVA_HOME/jre/lib/security/cacerts. All well known certificate authority root and intermediate certificates are available in the JDK truststore. |
| Keystore | A password-protected repository to hold client or private certificates. Since this store holds private keys, it is imperative that the store resides in a secure location. |
| Certificate chain | A certificate chain is an ordered list of certificates ending with the root certificate. For trust to be established, the entire certificate chain is traversed. Each certificate is validated by finding the public key of the next issuing certificate authority or intermediate certificate authority, until the root certificate is reached. Certificate chains are usually cached to validate the certificate locally. |

| Tool | Description |
|---|---|
keytool | A JDK utility used to perform CRUD operations on a truststore and keystore and to administer certificates. All the commands require the password that was used to create the store. Consult your Java truststore documentation for the default password. |
openssl | This is a robust, commercial-grade, full-featured toolkit for the TLS and SSL protocols. It is also a general-purpose cryptography library. |
Commands to Create a Client Certificate with the keytool Utility
Commonly usedkeytoolCaution:
Replace the italicized variables in the commands below with values appropriate to your environment.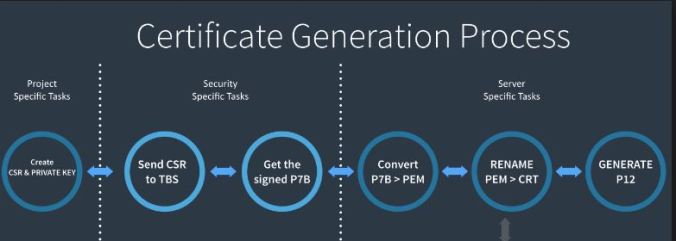
| Description | Command |
|---|---|
| List the entire contents of the store | keytool -list -keystore path_to_the_keystore |
| List the contents in the store for a specific alias | keytool -list -keystore path_to_the_keystore -alias alias_name |
| View the contents of a certificate | keytool -printcert -v -file name_of_the_file |
| Export a certificate from the store | keytool -export -alias alias_name -file certificate_name -keystore path_to_the_store |
| Import a new certificate into the store | keytool -import -trustcacerts -file path_to_the_certificate -alias alias_name -keystore path_to_the_store |
To create a client certificate:
Caution:
Italicized variables indicate placeholder variables for which you must supply particular values. If you copy the commands below, ensure that you replace the variables shown in italics with values appropriate to your environment.- Go to the Java
bindirectory. - Enter the following command to create a JKS keystore to hold the certificates.
- When prompted, change the values provided based on your company's security policy.
- Verify the existence of the JKS keystore file.
- Create a certificate that is ready to be signed.
- List the JKS keystore and certificate files in the directory.
- Validate your CSR file at the following site.
- Provide the
.csrcertificate file to a signing authority. A signed certificate and any root and intermediate certificates are signed and returned by the authority. A self-signed certificate can be used for testing, but is not allowed in a production environment. - If you have root and intermediate certificates, perform the following substeps. Otherwise, go to Step 10.
- If you have a root certificate, enter the following command to import the signed root certificate.
The following example is what you see when importing the DigiCert root certificate.
- If you have an intermediate certificate, enter the following command to import the signed intermediate certificate.
- If you have a root certificate, enter the following command to import the signed root certificate.
- If you have only a single certificate, enter the following command to import the signed certificate.
- Check if all the certificates are in the store.
- Export the public certifcate.
- Export the public certificate to provide to the server.
- Import the new keystore into Oracle Integration as an X509 identity certificate.
- List the entire contents of the store.
Example: Create a Client Certificate with the keytool Utility
This section provides an example of how to create a client certificate. It uses actual file names. Replace those names with values appropriate to your environment.
- Enter the following command to create a JKS keystore to hold the certificates. Where the following values are entered for this example:
-aliasis theoicclientkeystore alias.-keystoreis theidentityKeystore.jkskeystore file.
- When prompted, change the values provided based on your company's security policy.
- Verify the existence of the JKS keystore file.
- Create a certificate that is ready to be signed.Where the following values are entered for this example:
-aliasis theoicclientkeystore alias.-keystoreis theidentityKeystore.jkskeystore file.-fileis theoicclient.csrcertificate file.
- List the JKS keystore and certificate files in the directory.
- Validate your
.csrcertificate file at the following site. - Provide the
.csrcertificate file to a signing authority. The certificate and any root and intermediate certificates are signed and returned by the authority. A self-signed certificate can be used for testing, but is not allowed in a production environment. - If you have root and intermediate certificates, perform the following substeps. Otherwise, go to Step 9.
- If you have a root certificate, enter the following command to import the signed root certificate.Where the following values are entered for this example:
-keystoreis theidentityKeystore.jkskeystore file.-fileis theDigiCertGlobalRootCA.crtsigned root certificate file.-aliasis theDigiCertCARootalias.
- If you have an intermediate certificate, enter the following command to import the signed intermediate certificate.Where the following values are entered for this example:
-keystoreis theidentityKeystore.jkskeystore file.-fileis theDigiCertGlobalInterCA.crtsigned intermediate certificate.-aliasis theDigiCertCAInteralias.
- If you have a root certificate, enter the following command to import the signed root certificate.
- If you have only a single certificate, enter the following command to import the signed certificate.Where the following values are entered for this example:
-keystoreis theidentityKeystore.jkskeystore file.-fileis themy_company_signedcert.pemsigned certificate.-aliasis theoiclientalias.
- Check if all the certificates are in the store.
- Export the public certificate corresponding to the private identity certificate. Where the following values are entered for this example:
-aliasis theoicclientkeystore alias.-keystoreis theidentityKeystore.jkskeystore file.-fileis themy_company_signedcert.pempublic certificate file.
- Import the new keystore (
.jksfile) into Oracle Integration as an X509 identity certificate. - List the entire contents of the store.
Manage Certificates with openSSL
Commonly used openssl commands are as follows:
| Description | Command |
|---|---|
| Check a certificate | openssl x509 -in certificate_name -text -noout |
| Get all certificates from a server | openssl s_client -connect host:ssl_port -showcerts |
| Convert a DER format certificate to PEM format | openssl x509 -inform der -in path_to_DER_certificate -out path_to_PEM_certificate |
Convert a .pfx file to a JKS store | keytool -importkeystore -srckeystore path_to_.pfx_file -srcstoretype pkcs12 -destkeystore path_to_the_jks_file -deststoretype JKS -srcstorepass pfx_passwd -deststorepass pfx_passwd |
Convert a .jks file to PKCS12 format | keytool -importkeystore -srckeystore path_to_.jks_file -destkeystore full_path_to_.p12_file-srcstoretype JKS - deststoretype PKCS12 -deststorepass pkcs12_store_password |
Extract a private key from a .pfx file | openssl pkcs12 -info -in path_to_.pfx_file -nodes -nocerts -out private_key_file_name |
Extract a public certificate from a .pfx file | openssl pkcs12 -in path_to_.pfx_file -out path_to_certificate_file -nokeys |
Certificate Management - Two-Way SSL or mTLS
See Debugging SSL/TLS Connections.
To upload an identity certificate:
- In the navigation pane, select Home > Settings > Certificates.
- Click Upload.
- Set the alias name to the alias listed in the keystore for the identity certificate. (Use
keytool -listto see the contents of the keystore.) - Make sure the certificate category is set to Identity.
- Upload the client certificate file in JKS format.
- Enter the keystore and key passwords used to create the JKS store. If there is a mismatch in the passwords, Oracle Integration cannot access the identity certificates.
- Create a new adapter connection (SOAP Adapter or REST Adapter connection) in Oracle Integration.
- On the Connections page, select the two-way SSL checkbox and associate the alias required by the connection to use to complete the SSL connection. This alias must match the value that was entered in the Upload Certificate dialog.
To test Mutual TLS authentication (mTLS):
- Test access to the endpoint from the browser first. Import the client certificate in
.p12format into the browser of choice. - Enter the endpoint in the browser bar and press Enter. A message is displayed asking you to use the client certificate that was imported.
- Follow the prompts in the message. If the certificate is valid, content is loaded in the browser.
- If the browser test was successful, test the REST/SOAP adapter connection in Oracle Integration.
General commands

Convert Pem To Jks Windows
Openssl x509 -inform der -in pathtoDERcertificate-out pathtoPEMcertificate Convert a.pfx file to a JKS store. To convert the PEM-format keys to Java KeyStores: Convert the certificate from PEM to PKCS12, using the following command: openssl pkcs12 -export -out eneCert.pkcs12 -in eneCert.pem. You may ignore the warning message this command issues. Enter and repeat the export password.
You can obtain the client certificate in a variety of ways. Select the method that is best for your environment. For example, you can obtain the certificate directly from many certificate authorities. The steps in this section describe how to generate a certificate signing request (CSR) and have it signed by a well known certificate authority.
Note:
Inbound (trigger-based) two-way SSL is not supported.Commonly Used Terms and Tools
| Term | Description |
|---|---|
| Secure socket layer (SSL) and Transport Layer Security (TLS) | SSL and TLS, its successor, are protocols for establishing authenticated and encrypted links between networked computers. |
| Digital certificate | A data file that holds the cryptographic key provided to an organization or entity by a trusted authority. A simple analogy is a driver's license. The license uniquely identifies the person to whom it is issued. The license is issued by the DMV, a trusted authority. |
| Certificate | A public key and private key form a pair used to encrypt and decrypt data. Public keys can be freely given to anyone who needs to securely exchange data. Private keys must never be shared and must be stored securely. If private keys are listed or compromised, the issuing certificate authority must be notified so they can be added to the certificate revocation list. |
| Certificate authority (or certification authority) | An entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. |
| Certificate encoding/formats |
|
| TrustStore | A password-protected repository for trust or public certificates. The default location in Java is $JAVA_HOME/jre/lib/security/cacerts. All well known certificate authority root and intermediate certificates are available in the JDK truststore. |
| Keystore | A password-protected repository to hold client or private certificates. Since this store holds private keys, it is imperative that the store resides in a secure location. |
| Certificate chain | A certificate chain is an ordered list of certificates ending with the root certificate. For trust to be established, the entire certificate chain is traversed. Each certificate is validated by finding the public key of the next issuing certificate authority or intermediate certificate authority, until the root certificate is reached. Certificate chains are usually cached to validate the certificate locally. |
| Tool | Description |
|---|---|
keytool | A JDK utility used to perform CRUD operations on a truststore and keystore and to administer certificates. All the commands require the password that was used to create the store. Consult your Java truststore documentation for the default password. |
openssl | This is a robust, commercial-grade, full-featured toolkit for the TLS and SSL protocols. It is also a general-purpose cryptography library. |
Commands to Create a Client Certificate with the keytool Utility
Commonly usedkeytool commands are as follows. Caution:
Replace the italicized variables in the commands below with values appropriate to your environment.| Description | Command |
|---|---|
| List the entire contents of the store | keytool -list -keystore path_to_the_keystore |
| List the contents in the store for a specific alias | keytool -list -keystore path_to_the_keystore -alias alias_name |
| View the contents of a certificate | keytool -printcert -v -file name_of_the_file |
| Export a certificate from the store | keytool -export -alias alias_name -file certificate_name -keystore path_to_the_store |
| Import a new certificate into the store | keytool -import -trustcacerts -file path_to_the_certificate -alias alias_name -keystore path_to_the_store |
To create a client certificate:
Caution:
Italicized variables indicate placeholder variables for which you must supply particular values. If you copy the commands below, ensure that you replace the variables shown in italics with values appropriate to your environment.- Go to the Java
bindirectory. - Enter the following command to create a JKS keystore to hold the certificates.
- When prompted, change the values provided based on your company's security policy.
- Verify the existence of the JKS keystore file.
- Create a certificate that is ready to be signed.
- List the JKS keystore and certificate files in the directory.
- Validate your CSR file at the following site.
- Provide the
.csrcertificate file to a signing authority. A signed certificate and any root and intermediate certificates are signed and returned by the authority. A self-signed certificate can be used for testing, but is not allowed in a production environment. - If you have root and intermediate certificates, perform the following substeps. Otherwise, go to Step 10.
- If you have a root certificate, enter the following command to import the signed root certificate.
The following example is what you see when importing the DigiCert root certificate.
- If you have an intermediate certificate, enter the following command to import the signed intermediate certificate.
- If you have a root certificate, enter the following command to import the signed root certificate.
- If you have only a single certificate, enter the following command to import the signed certificate.
- Check if all the certificates are in the store.
- Export the public certifcate.
- Export the public certificate to provide to the server.
- Import the new keystore into Oracle Integration as an X509 identity certificate.
- List the entire contents of the store.
Example: Create a Client Certificate with the keytool Utility
This section provides an example of how to create a client certificate. It uses actual file names. Replace those names with values appropriate to your environment.
- Enter the following command to create a JKS keystore to hold the certificates. Where the following values are entered for this example:
-aliasis theoicclientkeystore alias.-keystoreis theidentityKeystore.jkskeystore file.
- When prompted, change the values provided based on your company's security policy.
- Verify the existence of the JKS keystore file.
- Create a certificate that is ready to be signed.Where the following values are entered for this example:
-aliasis theoicclientkeystore alias.-keystoreis theidentityKeystore.jkskeystore file.-fileis theoicclient.csrcertificate file.
- List the JKS keystore and certificate files in the directory.
- Validate your
.csrcertificate file at the following site. - Provide the
.csrcertificate file to a signing authority. The certificate and any root and intermediate certificates are signed and returned by the authority. A self-signed certificate can be used for testing, but is not allowed in a production environment. - If you have root and intermediate certificates, perform the following substeps. Otherwise, go to Step 9.
- If you have a root certificate, enter the following command to import the signed root certificate.Where the following values are entered for this example:
-keystoreis theidentityKeystore.jkskeystore file.-fileis theDigiCertGlobalRootCA.crtsigned root certificate file.-aliasis theDigiCertCARootalias.
- If you have an intermediate certificate, enter the following command to import the signed intermediate certificate.Where the following values are entered for this example:
-keystoreis theidentityKeystore.jkskeystore file.-fileis theDigiCertGlobalInterCA.crtsigned intermediate certificate.-aliasis theDigiCertCAInteralias.
- If you have a root certificate, enter the following command to import the signed root certificate.
- If you have only a single certificate, enter the following command to import the signed certificate.Where the following values are entered for this example:
-keystoreis theidentityKeystore.jkskeystore file.-fileis themy_company_signedcert.pemsigned certificate.-aliasis theoiclientalias.
- Check if all the certificates are in the store.
- Export the public certificate corresponding to the private identity certificate. Where the following values are entered for this example:
-aliasis theoicclientkeystore alias.-keystoreis theidentityKeystore.jkskeystore file.-fileis themy_company_signedcert.pempublic certificate file.
- Import the new keystore (
.jksfile) into Oracle Integration as an X509 identity certificate. - List the entire contents of the store.
Manage Certificates with openSSL
Commonly used openssl commands are as follows:
| Description | Command |
|---|---|
| Check a certificate | openssl x509 -in certificate_name -text -noout |
| Get all certificates from a server | openssl s_client -connect host:ssl_port -showcerts |
| Convert a DER format certificate to PEM format | openssl x509 -inform der -in path_to_DER_certificate -out path_to_PEM_certificate |
Convert a .pfx file to a JKS store | keytool -importkeystore -srckeystore path_to_.pfx_file -srcstoretype pkcs12 -destkeystore path_to_the_jks_file -deststoretype JKS -srcstorepass pfx_passwd -deststorepass pfx_passwd |
Convert a .jks file to PKCS12 format | keytool -importkeystore -srckeystore path_to_.jks_file -destkeystore full_path_to_.p12_file-srcstoretype JKS - deststoretype PKCS12 -deststorepass pkcs12_store_password |
Extract a private key from a .pfx file | openssl pkcs12 -info -in path_to_.pfx_file -nodes -nocerts -out private_key_file_name |
Extract a public certificate from a .pfx file | openssl pkcs12 -in path_to_.pfx_file -out path_to_certificate_file -nokeys |
Certificate Management - Two-Way SSL or mTLS
See Debugging SSL/TLS Connections.
To upload an identity certificate:
- In the navigation pane, select Home > Settings > Certificates.
- Click Upload.
- Set the alias name to the alias listed in the keystore for the identity certificate. (Use
keytool -listto see the contents of the keystore.) - Make sure the certificate category is set to Identity.
- Upload the client certificate file in JKS format.
- Enter the keystore and key passwords used to create the JKS store. If there is a mismatch in the passwords, Oracle Integration cannot access the identity certificates.
- Create a new adapter connection (SOAP Adapter or REST Adapter connection) in Oracle Integration.
- On the Connections page, select the two-way SSL checkbox and associate the alias required by the connection to use to complete the SSL connection. This alias must match the value that was entered in the Upload Certificate dialog.
To test Mutual TLS authentication (mTLS):
- Test access to the endpoint from the browser first. Import the client certificate in
.p12format into the browser of choice. - Enter the endpoint in the browser bar and press Enter. A message is displayed asking you to use the client certificate that was imported.
- Follow the prompts in the message. If the certificate is valid, content is loaded in the browser.
- If the browser test was successful, test the REST/SOAP adapter connection in Oracle Integration.
General commands
1. create JKS keystore
keytool -genkey -alias localhostkey -keystore localhost.keystore -storepass password
-keypass password -dname 'CN=localhost,OU=QE,O=example.com,L=Brno,C=CZ'
2. convert localhost.keystore to pkcs12
keytool -importkeystore -srckeystore localhost.keystore -destkeystore localhost.p12
-srcstoretype jks -deststoretype pkcs12 -srcstorepass password -deststorepass password
3. convert keystore to PEM
openssl pkcs12 -in localhost.p12 -out localhost.pem
4. just private key
openssl pkcs12 -in localhost.p12 -out localhost-privkey.pem -nocerts -nodes
5. pem file with just certificate
openssl pkcs12 -in localhost.p12 -out localhost-cert.pem -clcerts -nokeys
Creating a CA authority certificate and adding it into keystore
openssl.cnf file:
To create a CA key pair:
Convert Pem To Jks Using Keytool
To import in into a keystore:
Creating a multiple hosts (SAN) private key, signing it with CA and storing in keystore/truststore
(Note JDK7 keytool is required to handle extension syntax):
Create Jks From Pem
Creating a key pair:
Creating a certification request:
Sign it:
Import it into keystore:
Creating a signed X509 certificate for usage in browsers
Create a certificate request:
Openssl Pem To Jks
Sign it:
Openssl Convert Pem To Jks
Create X509 in PKCS12 format:

